Set up your project
- New project
- Existing Next.js project
Start from the vercel-template.
Create your Restate + Vercel repository
Configure Vercel project
With the GitHub repository set up, go over to the Vercel dashboard to create the project. For Restate to push requests to the Vercel project, you need Vercel Generated URLs to be accessible by Restate. You have two alternatives:- Disable Vercel Authentication for the project, making its URLs publicly accessible.
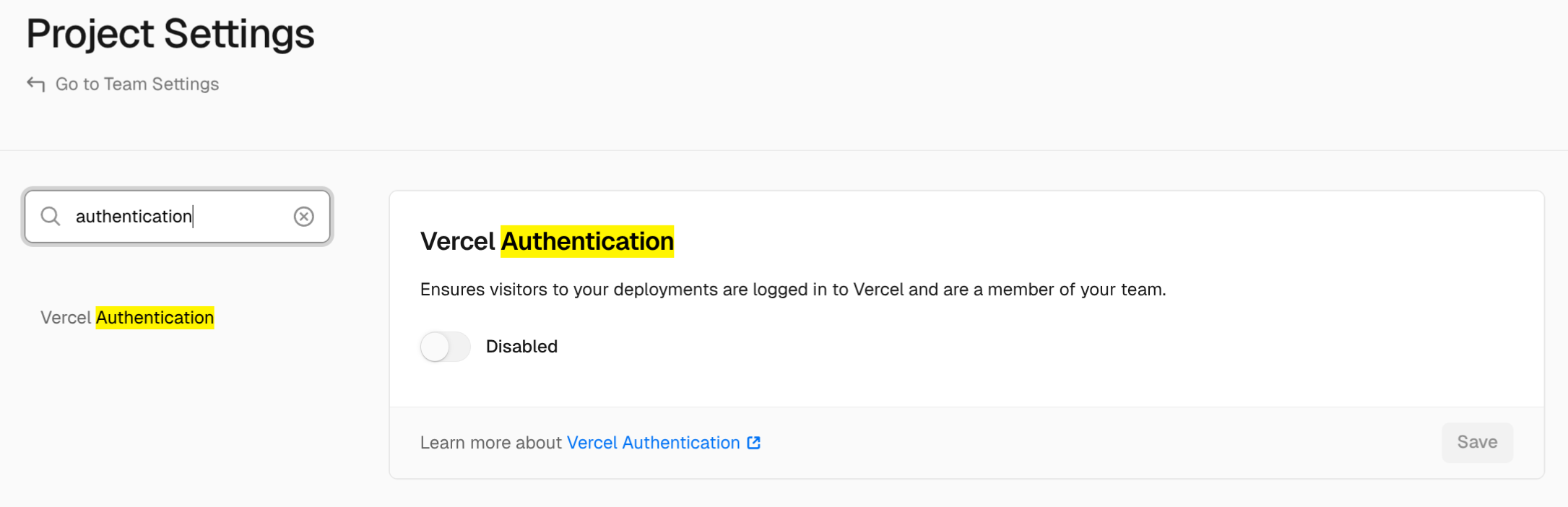
- Enable Protection Bypass for Automation. This makes the URLs accessible only if the
x-vercel-protection-bypassheader is provided with the right value.
Register the service to Restate
In order for Restate to push requests to your services, you need to register the service to Restate using the CLI or UI. Make sure to register the Commit URL so that Restate can address specific Vercel deployments:Restate identity keys (for Restate Cloud)
In order to make sure only a specific Restate Cloud environment can push requests to your Vercel deployment, head over to your Restate Cloud Dashboard to set up Restate identity keys.Restate Cloud > Developers > Security
Set up Restate identity keys
CI/CD Automation
You can set up automation to automatically register new Restate service versions every time a Vercel deployment gets promoted:RESTATE_ADMIN_URL: The Admin URL. You can find it in Developers > Admin URLRESTATE_AUTH_TOKEN: Your Restate Cloud auth token. To get one, go to Developers > API Keys > Create API Key, and make sure to select Admin for the role
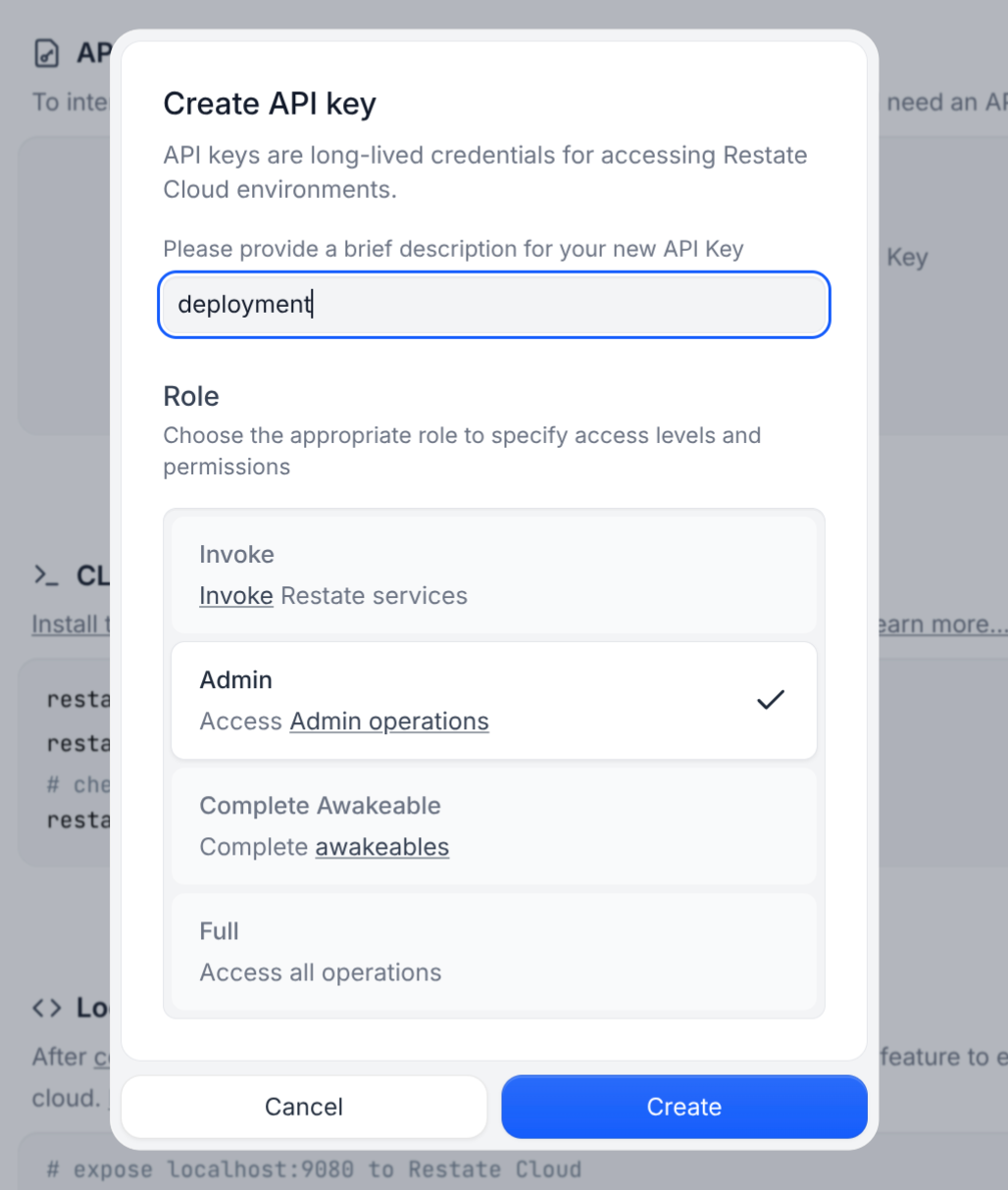
- If you set up the Protection Bypass for Automation as described above, add the secret
VERCEL_PROTECTION_BYPASS_TOKENwith the token value
Self-hosted Restate
Self-hosted Restate
You can use this workflow with Self-hosted Restate as well,
just make sure to correctly set up
RESTATE_AUTH_TOKEN and RESTATE_ADMIN_URL to reach your Restate cluster.